Masquer
Compliance-Centric Data Gateway

Masquer sits between your data and your application servers. Personal data is masked before external systems — remote contractor teams, analytics platforms, third-party integrations — ever have access. The private data problem is solved right at the source, so it can never have a downstream impact.
The Problem
Organizations handling sensitive data face an impossible workflow: copy production data, scrub PII, re-upload, repeat. Every copy doubles your storage costs. Every scrub takes engineering time. Every duplicate environment is another attack surface. Cloud providers charge by data volume — so compliance means paying more for less.
Zero-Copy Masking
Masquer masks data in-place. No copies, no duplicate infrastructure, no ETL pipelines. Because we intercept and mask at read-time, your compliant infrastructure doesn't cost significantly more than your existing setup. You get privacy without paying the "compliance tax" on storage and compute.
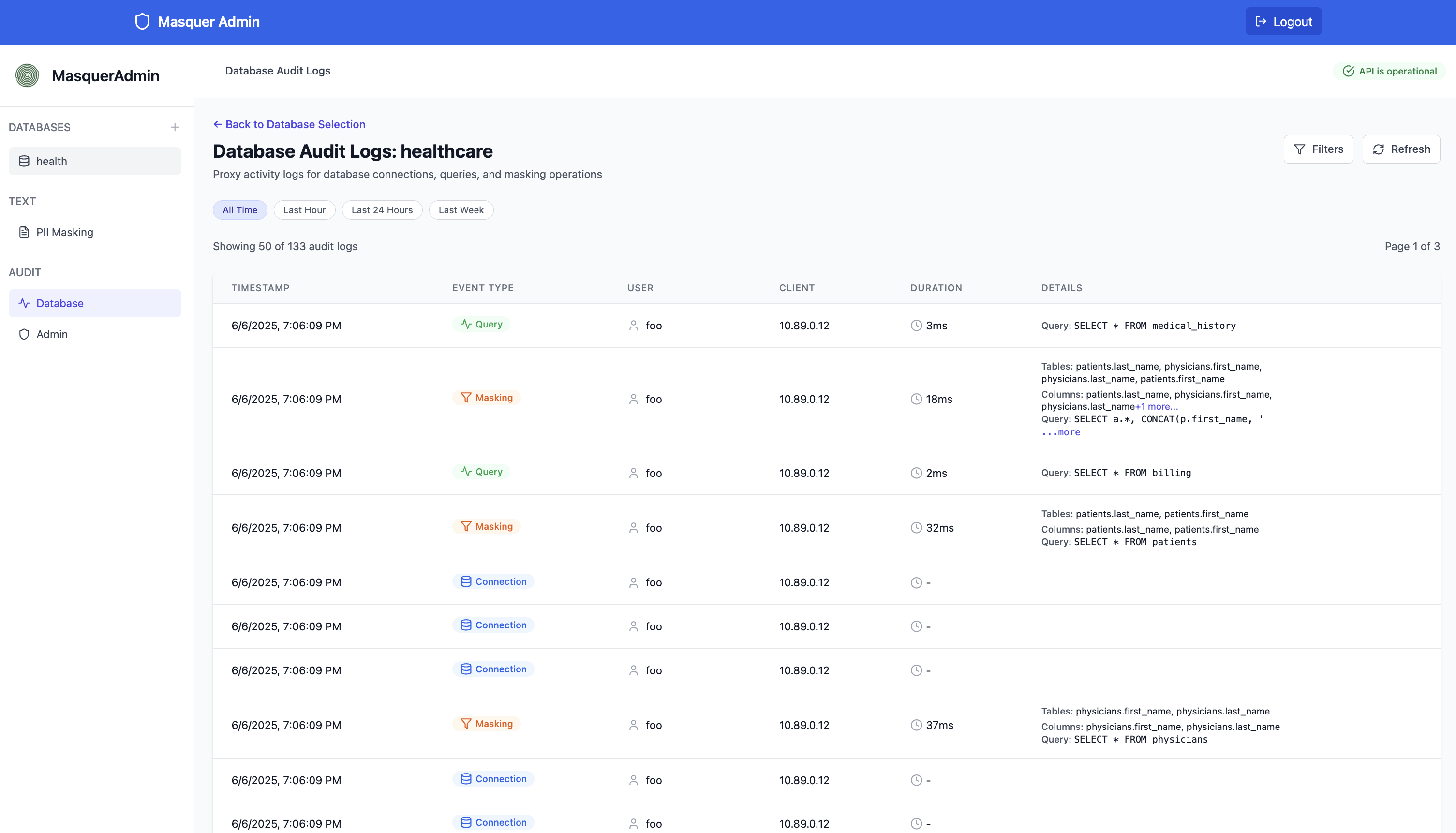
Built-In Access Logging
Because every data request passes through Masquer, we log who accessed private data, when, and what they saw. Audit trails are automatic — not bolted on after the fact. Your compliance team gets the evidence they need without chasing down access records across systems.
Use Cases
- Data Analytics: Run queries on production data without exposing PII to analysts or BI tools
- Third-Party Contractors: Give remote teams real data access with privacy guarantees — no sanitized copies
- In-System Permissions: Manage field-level visibility through Masquer instead of building access controls into every application
- Development & QA: Build and test against production-shaped data without compliance risk
Compliance Value
Masquer gives auditors a clear picture: private data is protected from third-party access at the infrastructure level. From the contract to the tech systems — demonstrable, auditable protection.
Relevant frameworks: SOC 2 CC6.1/CC6.3, ISO 27001 A.9/A.18, NIST AC-1/AC-3/AC-6/SC-28, HIPAA, CCPA, GDPR.
How It Works
PII Detection API
Start with our lightweight PII detection API for freeform text. Perfect for real-time processing and integration into existing workflows.
- Memory: Only ~2GB RAM required
- Speed: 500–700 tokens per second
- API: Simple REST endpoint integration
- Detection: Names, emails, SSNs, phone numbers, and more
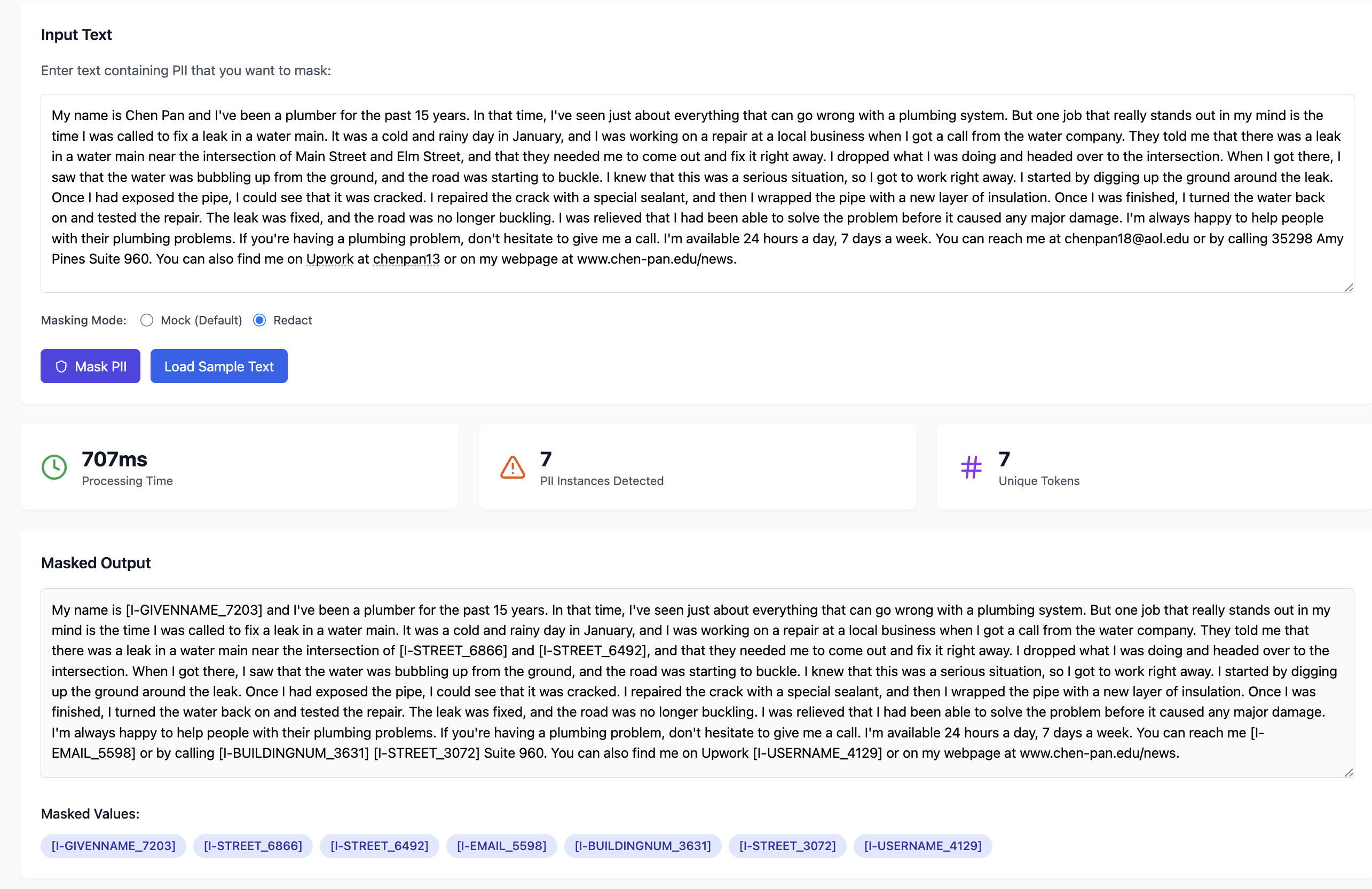
Intelligent Table Scanning
Using our PII detection engine, scan your database tables to identify columns containing sensitive information.
- Smart Detection: AI identifies potential PII columns
- Manual Review: You decide which columns to mask
- Granular Control: Select specific fields for protection
- Compliance Ready: Built-in governance workflows
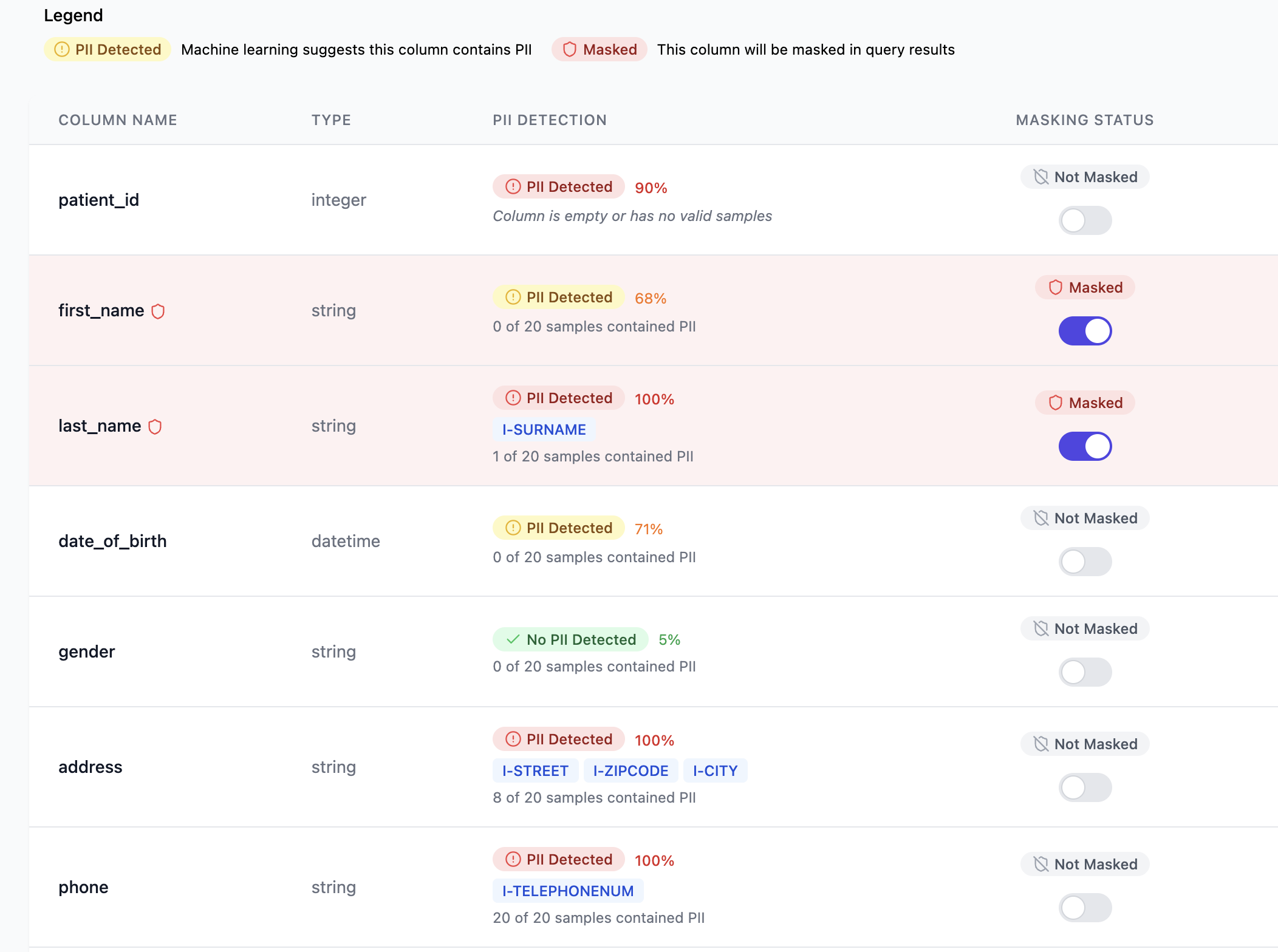
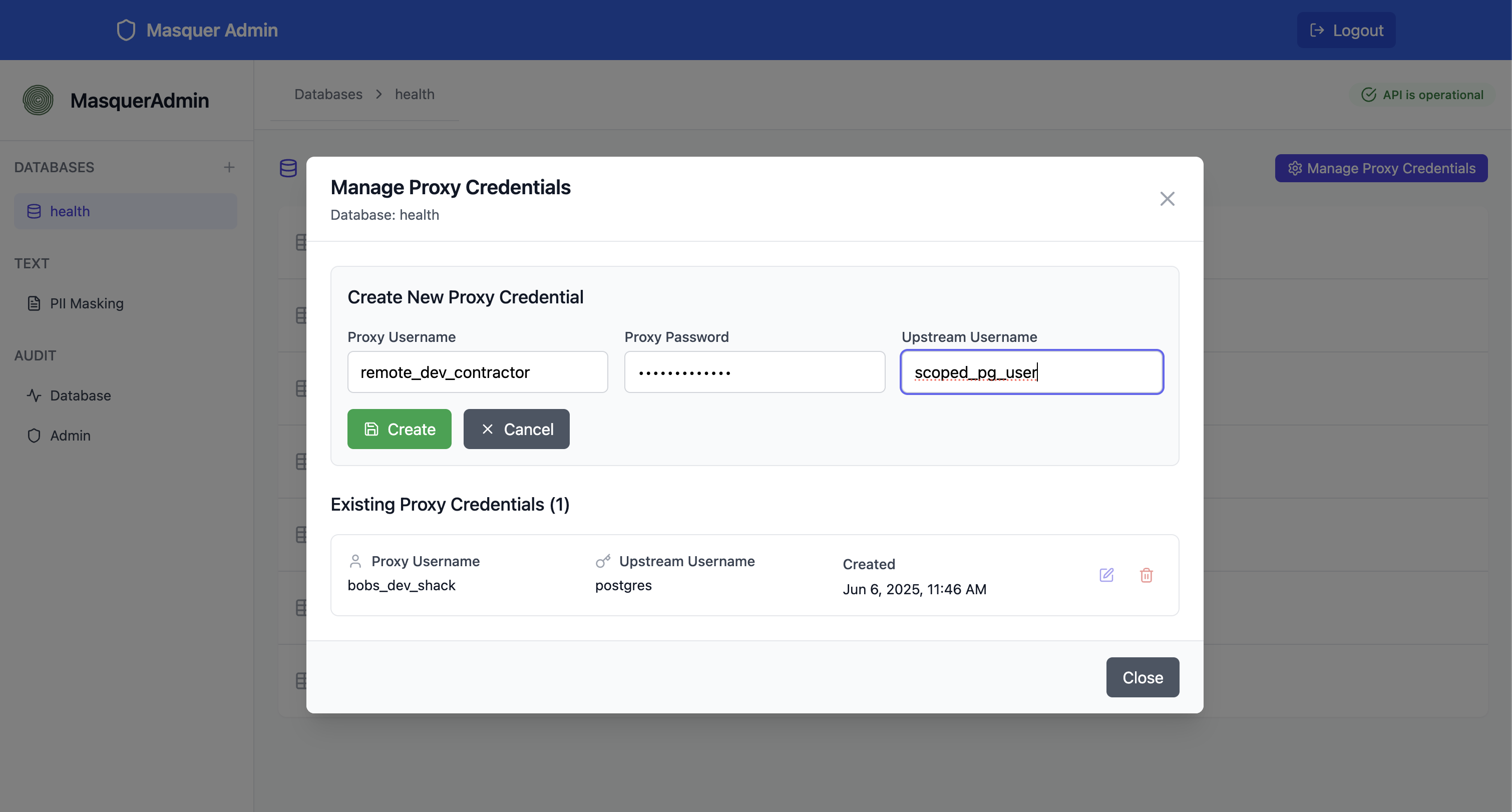
Secure Proxy Credentials
Create database credentials that third-party developers can use to access your data through Masquer's protective layer.
- Transparent Access: Standard database connections
- Real-time Masking: PII replaced on-the-fly
- Zero Code Changes: Works with existing applications
- Granular Permissions: Control what each user sees
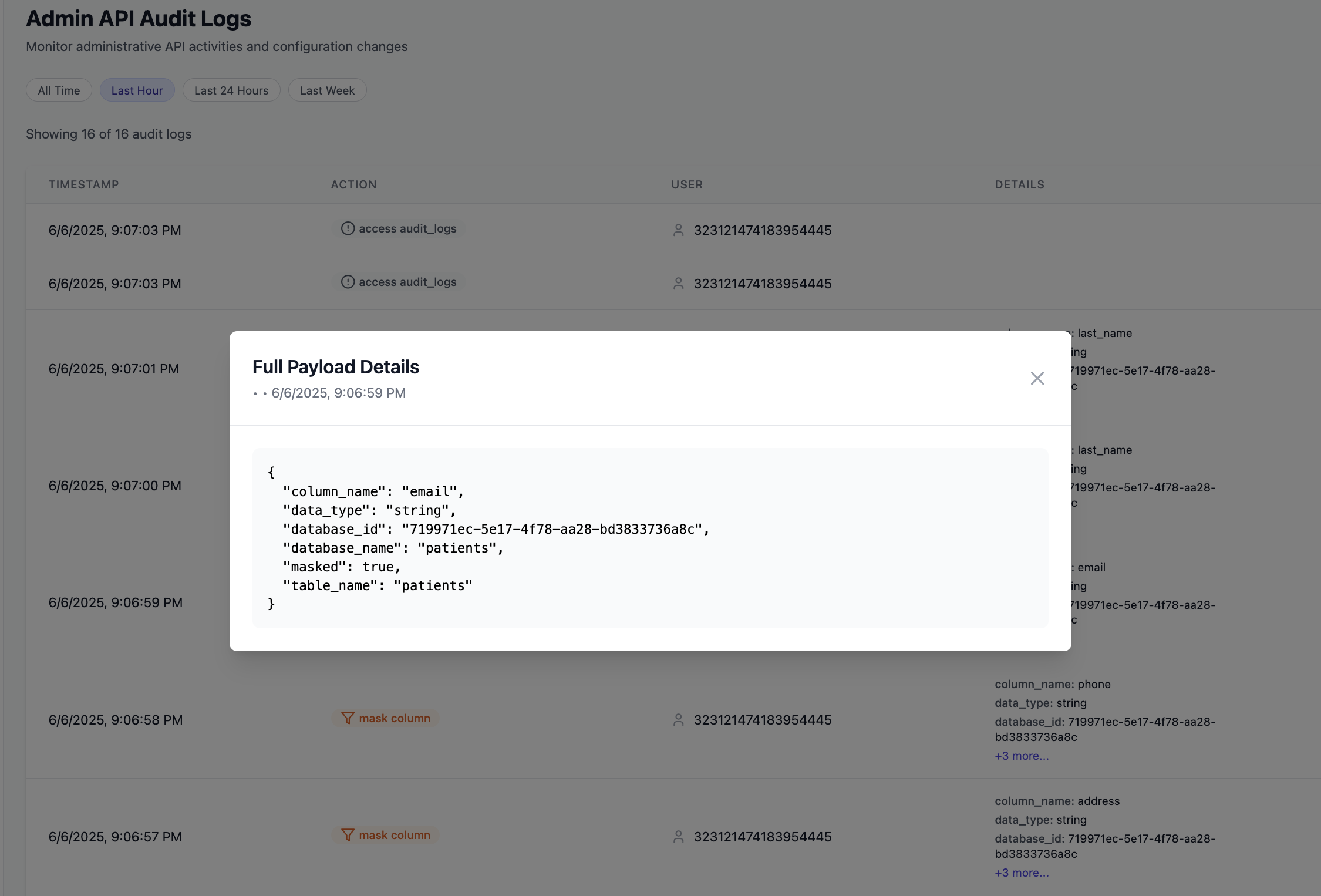
Comprehensive Admin Logging
Every administrative action on the Masquer system is automatically logged for compliance and audit purposes.
- Complete History: All configuration changes tracked
- User Attribution: Who made what changes when
- Compliance Ready: Meets SOC 2, HIPAA requirements
- Tamper Proof: Immutable audit records
Real-time Usage Monitoring
Monitor how developers interact with your masked data. See what gets detected, masked, and accessed in real-time.
- Query Tracking: Every database interaction logged
- Masking Details: What data was protected and how
- Performance Metrics: Response times and throughput
- Anomaly Detection: Unusual access patterns flagged
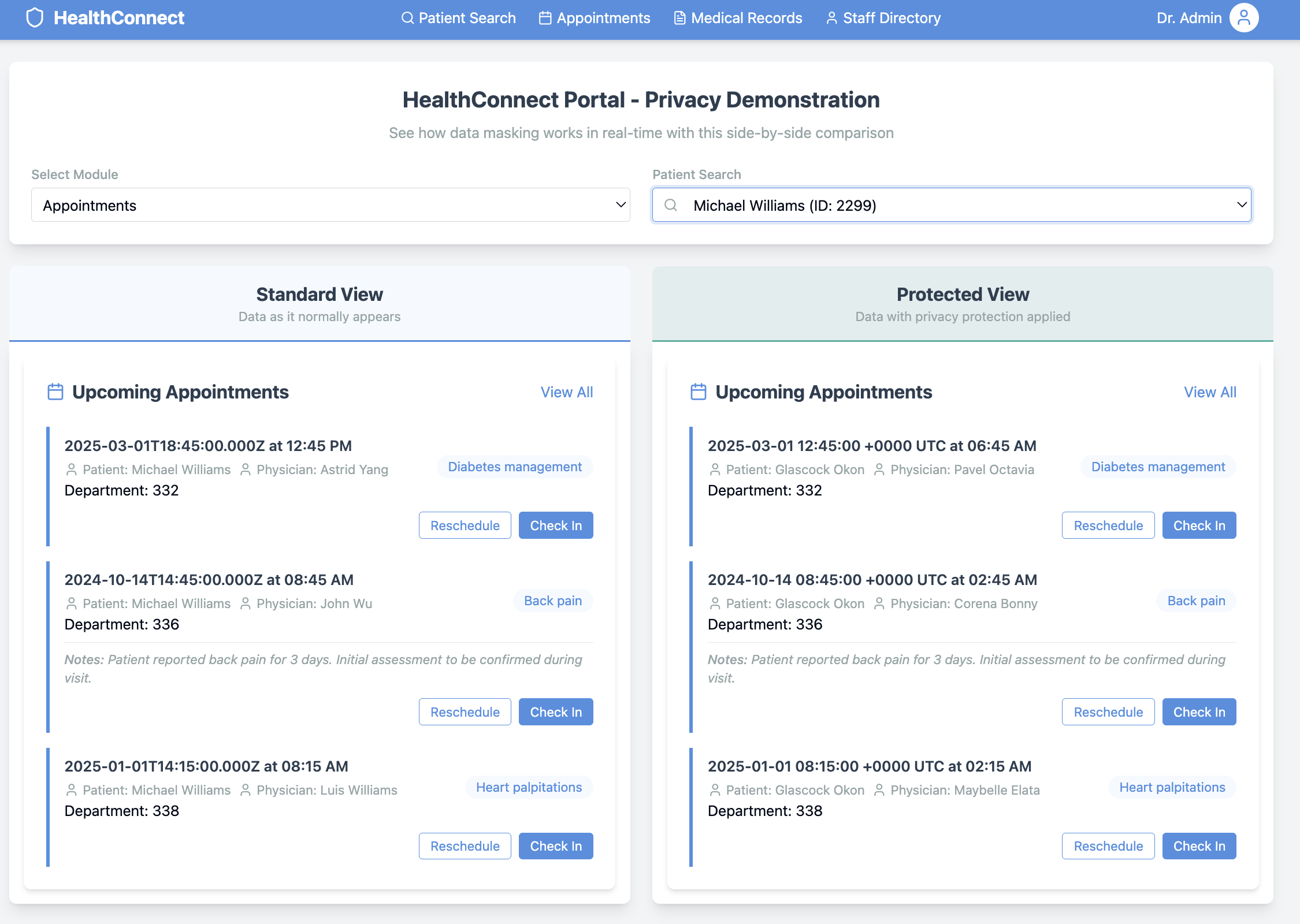
Privacy Without Compromise
The result: third-party teams get access to realistic, useful data while sensitive information remains completely protected.
- Faster Development: Teams get data access immediately
- Reduced Risk: No real PII in development environments
- Compliance Confidence: Built-in regulatory frameworks
- Innovation Enabled: Data access without privacy concerns
+ Tech Specs
Architecture
- Transparent PostgreSQL wire protocol proxy
- Real-time masking at read-time — no data duplication
- ML-powered PII detection (ONNX runtime, DeBERTa)
- Deterministic masking: same PII value → same masked output (referential integrity preserved)
- Format-preserving transformations: masked data still works in applications
- Runs entirely on-premise — zero data leaves your infrastructure
Technical Differentiators
- Go-native tensor operations: 90% memory reduction vs Python implementations
- Binary tokenizer: 10–100x faster startup than JSON tokenizers (standard)
- Session pooling with 512-token slicing for concurrent inference
- Up to 700 tok/sec on CPU
Ready to Mask Data, Not Innovation?
See how Masquer can enable secure data access for your teams while maintaining complete privacy compliance.

